![]() Manage Credentials
Manage Credentials
![]() Manage Credentials
Manage Credentials
|
<< Click to view the table of contents >> Navigation: Commands > Backstage >
|
Opens the Manage Credentials dialog box that allows you to enter a list of service accounts.
The accounts entered here will be usable by Active Directory One to perform operations that require administrative access, for example, to perform actions in the Active Directory One Agent service or can be used to grant delegation to manage users, groups or organizational units using the Delegated Users feature.
To ensure security, the credentials in this list are saved encrypted and can be used only by the application.
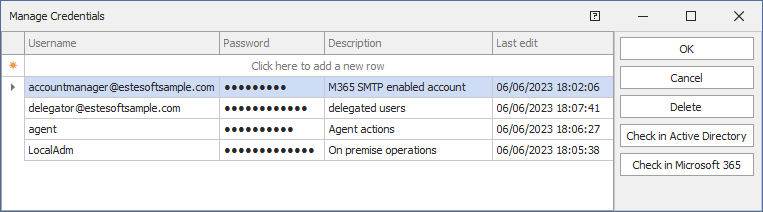
Before confirming an account entry, it is recommended to check with the buttons to the right in the dialog to verify that the user has been entered correctly and holds the necessary privileges to use the requested service.
•For security reasons, we recommend that you create specific accounts for the type of service you want to use; person accounts should not be used.
•If the application is using one of the accounts on this list and you remove it, related services or actions will stop working.
•Service users are used by Active Directory One to perform automated operations and therefore should not be associated with any type of multi-factor authentication.
|
This type of account can be used to send via SMTP protocol with standard authentication, and in all cases where only the username and password are required |
![]()
|
This type must contain an account that is present in the local Active Directory and has sufficient security privileges to perform the operations required in the context of use, e.g., it can be used as a delegator in the Delegated users feature or in the Active Directory Enrollment Strategy or Active Directory Exit Strategy features. |
|
This type must contain an account in the Entra ID database in a Microsoft 365 tenant and with sufficient security privileges to authorize the application to perform the necessary operations within the tenant, the scopes required by the application are described here.
Using the Log In to authentication portal button you are redirected online to the Microsoft 365 authentication portal where you are asked for your login credentials, once authenticated you are asked to authorize the scopes required by the application. Once the scopes are confirmed, the dialog box populates with the Tenant ID and username indicating that authentication was successful.
The Authorize button, can be used for a previously authenticated account to update the scopes needed for the application, for example if the software needs new permissions, or if the permissions have been changed manually and need to be applied again.
This account can be used, for example, in the Microsoft 365 License Assignment or Microsoft 365 Mailbox Configuration features and can also be used to send notifications via SMTP with modern OAuth authentication. In this case the user must have enabled “SMTP Authentication” in the tenant's user properties. To enable the user you can use the administration interface or via Powershell use the Set-CASMailbox command as in the following example: Set-CASMailbox -Identity sean@contoso.com -SmtpClientAuthenticationDisabled $false. See the Microsoft documentation on SMTP client authentication for more information.
If synchronization technologies such as Entra Connect are used, and the user is synchronized locally, the account configured here can also be used for local Active Directory management operations such as Active Directory Enrollment Strategy or Active Directory Exit Strategy
Note: In this process, the user's password is not obtained or stored within the application |
|
This type must contain a Google Workspace account that is a member of the Super Admin security group, this is required to authorize the application to perform the necessary operations within the tenant, the scopes required by the application are described here.
Using the Log in to the Google Workspace console button you will be redirected online to the Google Workspace authentication portal, here you will be prompted for the login credentials, once authenticated, on the Security->API Controls->Domain-wide Delegation page use the Add new command, copy and paste the Client ID and OAuth scopes into the respective fields.
This operation only needs to be done once in the tenant.
Once the operations are completed in Google Workspace and after clicking the OK button, a confirmation email is sent to the set email address. After confirming in the email it is necessary to wait up to 48 hours before the account set up is authorized.
During the authorization phase you can check the status of the operation using the Verify Account button in the Manage Credential dialog.
A single account can be authorized for each Google Workspace tenant.
These credentials can be used in the Google Workspace License Assignment and Google Workspace Mailbox Configuration features and in contexts where email notifications need to be sent.
Note: In this process, the user's password is not obtained or stored within the application |
|
This account type allows you to use the Twilio SendGrid SMTP service to send email notifications. It can be, for example, used in Active Directory Enrollment Strategy or Active Directory Exit Strategy. |
|
This Account type allows you to use the Amazon SES SMTP service to send email notifications. It can be used, for example, in Active Directory Enrollment Strategy or Active Directory Exit Strategy. |
See also: Active Directory One Agent - Delegated Users